Do you know there are more than 100 NoSQL databases are available today? Thanks to the open-source community. Which one have you heard of? MongoDB and Redis, probably! Yes, they are very popular. NoSQL is not a new thing; it was first introduced in 1998 by Carlo Strozzi. But lately, it has gained a lot of popularity with its usage in modern applications. And why not. It is fast and solves some of the traditional relational database issues. There are differences between SQL and NoSQL. If you are using a NoSQL database such as MongoDB and unsure if they are good for production, don’t expose vulnerabilities, misconfiguration, etc.. The following tools can help you find.
NoSQLMap
NoSQLMap is an open-source tiny utility based on Python, capable of auditing for finding misconfiguration and automating injection attacks. It supports the following databases at the moment.
MongoDB CouchDB Redis Cassandra
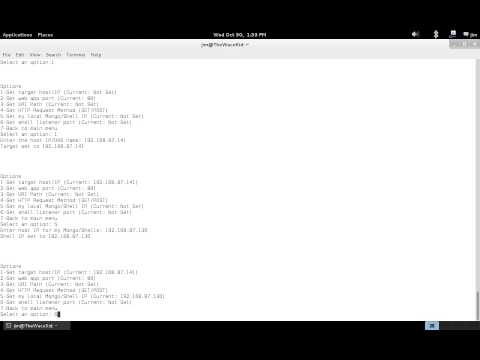
To install NoSQLMap, you need Git, Python, and Setuptools module, which you can install below on Ubuntu. Once Python is installed, then following to install NoSQLMAP. Once done, you can execute ./nosqlmap.py from the GIT cloned directory, which will prompt like below. You need to set the target by going to option 1 before testing. Check out below demo tutorial.
Mongoaudit
As you can guess by the name, it is specific for MongoDB. Mongoaudit is good for performing pentest to find a bug, misconfiguration, and potential risks. It checks against many best practices, including the following.
If MongoDB is running on the default port and the HTTP interface is enabled If secured with TLS, Authentication Authentication method CRUD operations
Installing Mongoaudit is easy. You can use the pip command. Once installed, execute mongoaudit command to run the scan. You will be prompted to select the scan level and enter MongoDB listener details.
Whatever tool you use to run a security scan against NoSQL databases, remember to be responsible. You got to ensure you are running against your own database instance or authorized to run the test. If you often work on NoSQL, you may be interested in exploring these clients to manage better productivity. And check out this article to find SQL injection vulnerability in a relational database.

![]()